Reading this blog post by Shawn Melton Introduction of Visual Studio Code for DBAs reminded me that whilst I use Visual Studio Code (which I shall refer to as Code from here on) for writing PowerShell and Markdown and love how easily it interacts with Github I hadn’t tried T-SQL. If you are new to Code (or if you are not) go and read Shawns blog post but here are the steps I took to running T-SQL code using Code
- Visual Studio Terraform Free
- Visual Studio Terraform 2020
- Visual Studio Code Terraform 12
- Visual Studio Terraform 0.12
To download Code go to this link https://code.visualstudio.com/download and choose your operating system. Code works on Windows, Linux and Mac
Once you have downloaded and installed hit CTRL SHIFT and P which will open up the command palette
Once you start typing the results will filter so type ext and then select Extensions : Install Extension
Which will open the Extensions tab ( You could have achieved the same end result just by clicking this icon)
But then you would not have learned about the command palette 🙂
- Terraform is a tool for creating infrastructure on Azure. Yeoman makes it easy to create Terraform modules. In this article, you learn how to do the following tasks: Create a base Terraform template using the Yeoman module generator.
- Terraform VSTS build task. Run terraform on the build server. The terraform task let you: Use a service endpoint to provide azure credentials; Use Azure blob storage for terraform remote backend; install terraform if not installed on build server; run terraform commands and arguments; Extra links. Get started with terraforms on azure.
- May 16, 2019 Visual Studio 2017/2019 utilizes a self signed certificate which is stored in the windows certificate store. Specifically, it uses a dotnet global tool built into.NET Core 2.1 to help with certs.
So, with the extensions tab open, search for mssql and then click install
Terraform This is a Visual Studio Code extension. Adds syntax support for the Terraform and Terragrunt configuration language. Jan 05, 2017 Reading this blog post by Shawn Melton Introduction of Visual Studio Code for DBAs reminded me that whilst I use Visual Studio Code (which I shall refer to as Code from here on) for writing PowerShell and Markdown and love how easily it interacts with Github I hadn't tried T-SQL.
Once it has installed the button will change to Reload so click it
And you will be prompted to Reload the window
Accept the prompt and then open a new file (CTRL N) and then change the language for the file.
You can do this by clicking CTRL K and then M (Not CTRL K CTRL M) or click the language button
And then choose SQL
This will start a download so make sure you are connected (and allowed to connect to the internet)
Once it has finished it will show this
And offer you the chance to read the release notes
Which you can get for any extension anytime by finding the extension in the extensions tab and clicking on it. This has links to tutorials as well as information about the release
The mssql extension enables Intellisence for T-SQL when you open a .sql file or when you change the language to SQL as shown above for a new file
Write your T-SQL Query and press CTRL SHIFT and E or Right Click and choose Execute Query. This will ask you to choose a Connection Profile (and display any existing profiles)
Choose Create Connection Profile and answer the prompts
The query will then run
You can then output the results to csv or json if you wish
You can find a video showing this whole process with some typos and an error here
Using SQL with VS Code
The tasks in this extension allow for running terraform cli commands from Azure Pipelines. The motivation for this extension was to provide terraform pipeline tasks that could execute on all build agent operating systems and provide guided task configuration.
Supported Commands
The Terraform CLI task supports executing the following commands
- version
- init
- validate
- plan
- apply
- destroy
- show
- refresh
- import
- output
- force-unlock
- fmt
- workspace (NEW)
Compatible with Linux Build Agents
The tasks can execute on all supported build agent operating systems including Ubuntu and MacOS.
Separate Task for Terraform Installation
The dedicated Terraform Installer task allows for complete control over how frequently and on which agents terraform is installed. This prevents from having to install terraform before executing each terraform task. However, if necessary, this can be installed multiple times to support pipelines that span multiple build agents
Install Latest Version
The installer task supports installing the latest terraform version by using the keyword latest as the version specified. This is the default option when the installer is added to a pipeline. Specifying latest will instruct the task to lookup and install the latest version of the terraform executable.
If terraformVersion not provided, task defaults to latest
Install Specific Version
Azure Service Connection / Service Principal Integration
When executing commands that interact with Azure such as plan, apply, and destroy, the task will utilize an Azure Service Connection to authorize operations against the target subscription. This is specified via the environmentServiceName input
Execute Azure CLI From Local-Exec Provisioner
When an azure service connection is provided and runAzLogin is set to true, the terraform cli task will run az login using the service connection credentials. This is intended to enable templates to execute az cli commands from a local-exec provisioner.
Setting runAzLogin to true will indicate the task should execute az login with specified service connection.
Setting runAzLogin to false will indicate the task should not execute az login with specified service connection.

runAzLogin will default to false when not specified; indicating the task should NOT run az login
This should allow the following template configuation to be run using this task
Remote, Local and Self-configured Backend State Support
The task currently supports the following backend configurations
- local (default for terraform) - State is stored on the agent file system.
- azurerm - State is stored in a blob container within a specified Azure Storage Account.
- self-configured - State configuration will be provided using environment variables or command options. Environment files can be provided using Secure Files Library in AzDO and specified in Secure Files configuration field. Command options such as
-backend-config=flag can be provided in the Command Options configuration field.
If azurerm selected, the task will prompt for a service connection and storage account details to use for the backend.
Automated Remote Backend Creation
The task supports automatically creating the resource group, storage account, and container for remote azurerm backend. To enable this, set the ensureBackend input to true and provide the resource group, location, and storage account sku. The defaults are 'eastus' and 'Standard_RAGRS' respectively. The task will utilize AzureCLI to create the resource group, storage account, and container as specified in the backend configuration.
Secure Variable Secrets
There are multiple methods to provide secrets within the vars provided to terraform commands. The commandOptions input can be used to specify individual -var inputs. When using this approach pipeline variables can be used as -var secret=$(mySecretPipelineVar). Additionally, either a terraform variables file or a env file secured in Secure Files Library of Azure DevOps pipeline can be specified. Storing sensitive var and env files in the Secure Files Library not only provides encryption at rest, it also allows the files to have different access control applied than that of the Source Repository and Build/Release Pipelines.
Secure Env Files
If the Secure Variables file name is *.env, it is referred as .env file. This task loads environment variables from the .env file.
.env file example
Terraform Output to Pipeline Variables
The TerraformCLI task supports running the Terraform output command. When this is run, pipeline variables will be created from each output variable emitted from the terraform output command. Sensitive variables will be set as secret pipeline variables and their values will not be emitted to the pipeline logs.
For example, an output variable named some_string will set a pipeline variable named TF_OUT_SOME_STRING.
This feature currently only supports primitive types string, bool, and number. Complex typed outputs such as tuple and object will be excluded from the translation.
Template has output defined
Pipeline configuration to run terraform output command
Use output variables as pipeline variables
Visual Studio Terraform Free
Note that $(TF_OUT_SOME_SENSITIVE_STRING) will be redacted as *** in the pipeline logs.
Terraform Plan View
The extension includes a feature to render terraform plans within the pipeline run summary. To use this feature publishPlanResults input must be provided when running terraform plan via the TerraformCLI task. Then input should be set to the name that should be assigned to the plan.
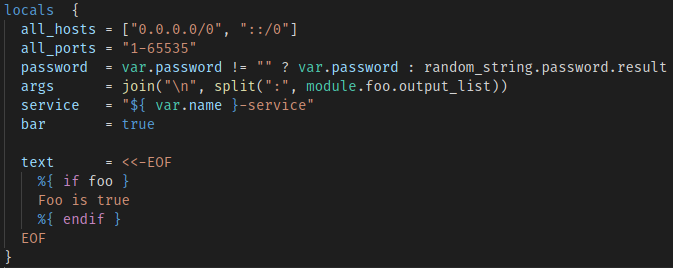
Important - When enabling publishPlanResults the -detailed-exitcode option will be added when running terraform plan if it was not already provided in the commandOptions input. This will cause TERRAFORM_LAST_EXITCODE to be 2 when plan includes changes; which is a successful exitcode. Additionally, warnings will be logged to the pipeline summary when changes are present as a means to alert that changes will be made if the templates are applied.
If the publishPlanResults input is not provided, then no plans will be published. In this case, the view will render empty with a message indicating no plans were found.
**Note The name set on publishPlanResults is only used for rendering in the view. It does not cause the cli to implicitly save plan output on the agent with that name.
Terraform Plan Change Detection
When running terraform plan with -detailed-exitcode, a pipeline variable will be set to indicate if any changes exist in the plan. TERRAFORM_PLAN_HAS_CHANGES will be set to true if plan detected changes. Otherwise, this variable will be set to false. This can be used in conjunction with Custom Condition expression under Control Options tab of the task to skip terraform apply if no changes were detected.
Run apply only if changes are detected.
Terraform Plan Destroy Detection
The task now has the ability to set a pipeline variable TERRAFORM_PLAN_HAS_DESTROY_CHANGES if a generated plan has destroy operations. To utilize this, run terraform plan and set the -out=my-plan-file-path to write the generated plan to a file. Then run terraform show and provide the path to the generated plan file in the Target Plan or State File Path input field. If show, detects a destroy operation within the plan file, then the pipeline variable TERRAFORM_PLAN_HAS_DESTROY_CHANGES will be set to true.
Visual Studio Terraform 2020
Run show to detect destroy operations
Skip apply if destroy operations
Workspaces (NEW)
Visual Studio Code Terraform 12
The task supports managing workspaces within pipelines. The following workspace subcommands are supported.
Visual Studio Terraform 0.12
Workspace Select
